Planet Earth… end of the 21st century: the Achab Corporation influences and dominates the globe using outstanding technologies, obtained via access to Gene.sys, a secret database of unknown origin…
The Breach is a competitive Net-Crawler game: You are a Breacher, a digital rebel who attempts to crack the Gene.sys database to steal secret information. Upgrade your Avatar and assign viruses, fight the Guards and rival Breachers!
2700+ Breachers connected to the Network! 20+ Stretch goals unlocked! 50+ miniatures included!
Last days! Campaign ends on June 9th!

You will receive all latest news about The Breach.
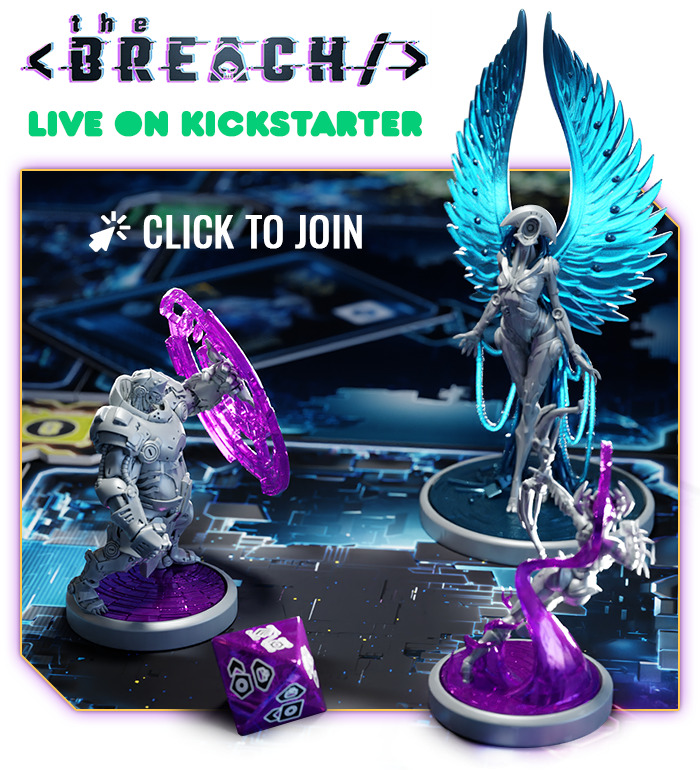
Spectacular two-component miniatures and stunning graphic creations
will allow you to fully immerse yourself in the game’s setting.

Do you want know more about The Breach?
2700+ Breachers connected to the Network! 20+ Stretch goals unlocked! 50+ miniatures included!
Last days! Campaign ends on June 9th!